The Optus Breach: How Not to PR
Optus, the second-largest telecommunications company in Australia, confirmed on September 22nd that roughly 9.8 million personal records of current and past customers were leaked. They had no additional info at the time, which left those affected feeling helpless and betrayed.
An unidentified person has taken responsibility for the hack. The hacker demanded $1 million to delete the data. Otherwise, they would release 10,000 personal records a day until they received payment.
The alleged hacker followed up on their threat - once. When payment was not received, they released 10,000 records that likely went straight to the dark web to piece together some profiles - a process whereby bots analyze whether criminals have enough information to target someone with scamming or identity theft. The hacker has since withdrawn their demand, apologized for their actions, and has not released any additional records.
Affected records include everything from phone numbers to driver’s licenses and passport numbers.
Table of Contents
Backlash
Investigating a breach is no small undertaking, and it’s impossible to know for certain if Optus acted slower than other industry giants would in an identical situation. However, their attitude and lackluster communication resulted in severe backlash from the Australian government and general public.
Optus framed itself as the victim of a cyberattack despite no evidence of how the personal records were accessed. In an interview with the Sydney Morning Herald, CEO Bayer Rosmarin said, “There has been no review and no report on the nature of what has occurred… so anyone saying anything about it is not talking from a position of knowledge.”
This attempt to control the narrative left government officials unimpressed.
Government Services Minister Bill Shorten told reporters, using a suitably Australian metaphor: “Optus senior management are kidding themselves if they want a medal for the way that they’ve been communicating. Not even a crocodile’s going to swallow that.”
The Situation Worsens
Two weeks later Optus provided additional info. After combing through logs, they claim that only 2.1 million personal records were exposed, of which 900,000 are expired. They said that all affected persons had been contacted, warned users not to open links from email or SMS, and recommended the My Optus app as the safest way to communicate with them.
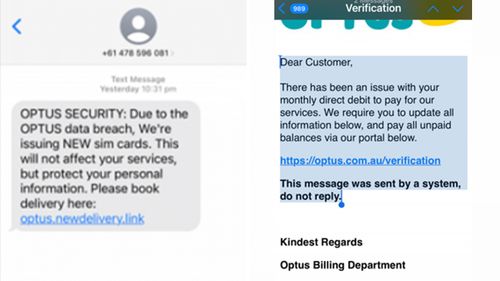
However, the leaked data goes back to 2017 and includes many ex-customers. How will these people be contacted safely? Does sending one email count as “contacted”? No one knows. And scammers are capitalizing on the confusion.
Customers are seeing phishing emails, phone calls, and SMS or social media messages asking users to order new SIM cards or update billing information in order to secure themselves from the attack.
The government agency Scamwatch took the initiative to warn customers about these scams. “Optus is not contacting people about their bills and asking you to update information.”
In the absence of other directions, people are scrambling to update their passports and driver’s license numbers.
How was the data exposed?
Knowledge of how the breach occurred is frustratingly scarce.
According to Security Boulevard, “Unconfirmed reports suggest that an API Gateway was being used by Optus. If so, that API gateway failed to sufficiently rate limit the attacker's access to Optus's sensitive data.”
Security Boulevard provides a good overview of possible API vulnerabilities that led to easy personal information extraction. Time will tell if this was the weak link.
Optus is noncommittal regarding whether or not they will release the full review being done by consultancy firm Deloitte. Perhaps this is Optus's ill-conceived attempt to make things seem less bad. If so, they failed to consider that the human imagination proliferates catastrophes, and the possibility that 2.1 million identities are compromised gives it ample fodder.
Optus is now attempting open communication through its website, but it may be too little too late to save face.
We’re waiting on the results of the investigation to form a picture of what you can do to prepare for future breaches of this nature, or how you can take action to mitigate risk now. Fingers crossed that the findings will get released to the public.
Optus has dug itself a bit of a hole. Government fines loom on the horizon, and user trust is eroded. We shall see how they choose to proceed.
To be continued…